Table of Contents
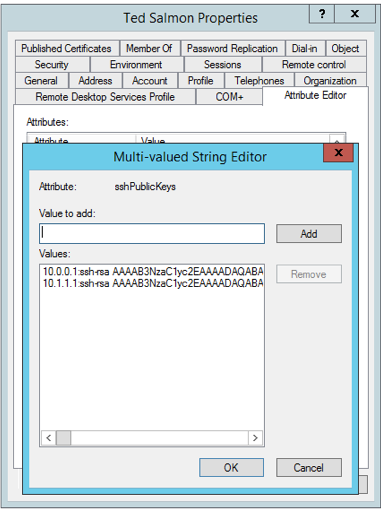
Decision Central provides an SSH keystore service to enable user SSH authentication. It provides a configurable default SSH keystore, extensible APIs (for custom implementations), and support for multiple SSH public keys formats. You can access the SSH Keys option from the Admin page to register your SSH public keys. A keystore is a repository of security certificates, that can hold your keys and certificates and encrypt them all with a password. In other words, a keystore is just like a hashtable which has an alias that identifies a certificate and then the certificate itself. The Java JDK maintains a CAC keystore in jre/lib/security/cacerts. It is because ssh-agent on Windows is using an older signing algorithm that your sever is. First, we gotta switch to Glassfish’s keystore and import the. Command line tools to compress and encrypt your keys. The certificate embed a Distinguish Name and other stuff to initialize a SSL communication between 2 entities. I think there is a confusion between SSL and SSH, and I am note sure it is possible that information stored in a keystore may be used for an SSH communication. – Francois Gergaud Jul.
Introduction
SSH can handle authentication using a traditional username and password combination or by using a public and private key pair. The SSH key pair establishes trust between the client and server, thereby removing the need for a password during authentication. While not required, the SSH private key can be encrypted with a passphrase for added security.
The PuTTY SSH client for Microsoft Windows does not share the same key format as the OpenSSH client. Therefore, it is necessary to create a new SSH public and private key using the PuTTYgen tool or convert an existing OpenSSH private key.
Requirements
- PuTTY SSH client for Microsoft Windows
- Remote server accessible over OpenSSH
Install PuTTY and PuTTYgen
Both PuTTY and PuTTYgen are required to convert OpenSSH keys and to connect to the server over SSH. These two tools can be downloaded individually or, preferably, as a Windows installer from the PuTTY Download Page.
Once the PuTTY Windows installer is downloaded, double-click the executable in the Download folder and follow the installation wizard. The default settings are suitable for most installations. Both PuTTY and PuTTYgen should now be accessible from the Windows Programs list.
Use Existing Public and Private Keys
If you have an existing OpenSSH public and private key, copy the id_rsa key to your Windows desktop. This can be done by copying and pasting the contents of the file or using an SCP client such as PSCP which is supplied with the PuTTY install or FileZilla.
Next launch PuTTYgen from the Windows Programs list.
- Click
Conversionsfrom the PuTTY Key Generator menu and selectImport key. - Navigate to the OpenSSH private key and click
Open. - Under
Actions/Save the generated key, selectSave private key. - Choose an optional passphrase to protect the private key.
- Save the private key to the desktop as
id_rsa.ppk.
If the public key is already appended to the authorized_keys file on the remote SSH server, then proceed to Connect to Server with Private Key.
Otherwise, proceed to Copy Public Key to Server.
Create New Public and Private Keys
Launch PuTTYgen from the Windows Programs list and proceed with the following steps.
- Under
Parameters, increase theNumber of bits in a generated key:to a minimum value of 2048. - Under
Actions/Generate a public/private key pair, clickGenerate. - You will be instructed to move the mouse cursor around within the PuTTY Key Generator window as a randomizer to generate the private key.
- Once the key information appears, click
Save private keyunderActions/Save the generated key. - Save the private key to the desktop as
id_rsa.ppk. - The box under
Key/Public key for pasting into OpenSSH authorized_keys file:contains the public key.
Copy Public Key to Server
The OpenSSH public key is located in the box under Key / Public key for pasting info OpenSSH authorized_keys file:. The public key begins with ssh-rsa followed by a string of characters.
- Highlight entire public key within the PuTTY Key Generator and copy the text.
- Launch PuTTY and log into the remote server with your existing user credentials.
Use your preferred text editor to create and/or open the
authorized_keysfile:Paste the public key into the
authorized_keysfile.Save the file and close the text editor.
Adjust the permissions of the
authorized_keysfile so that the file does not allow group writable permissions.Logout of the remote server.
Connect to Server with Private Key
Now it is time to test SSH key authentication. The PuTTYgen tool can be closed and PuTTY launched again.
- Enter the remote server Host Name or IP address under
Session. - Navigate to
Connection>SSH>Auth. - Click
Browse...underAuthentication parameters/Private key file for authentication. - Locate the
id_rsa.ppkprivate key and clickOpen. - Finally, click
Openagain to log into the remote server with key pair authentication.
Generating a KeyStore and TrustStore

The following sections explain how to create both a KeyStoreand a TrustStore (or import a certificate into an existing TrustStoresuch as the default Logical Host TrustStore in the location:
Ssh Keystore Linux
where <c:JavaCAPS> isthe directory where Java CAPS is installed and <MyDomain> isthe name of your domain. The primary tool used is keytool, but openssl isalso used as a reference for generating pkcs12 KeyStores.
For more information on openssl andavailable downloads, visit the following web site:
http://www.openssl.org.
Creating a KeyStore in JKS Format
This section explains how to create a KeyStore using theJKS format as the database format for both the private key, and theassociated certificate or certificate chain. By default, as specifiedin the java.security file, keytool usesJKS as the format of the key and certificate databases (KeyStore andTrustStores). A CA must sign the certificate signing request (CSR).The CA is therefore trusted by the server-side application to whichthe Adapter is connected.
Note –Itis recommended to use the default KeyStore
where <c:JavaCAPS> isthe directory where Java CAPS is installed and <MyDomain> isthe name of your domain.
To Generate a KeyStore

Perform the following command.
Once prompted, enter the information required to generatea CSR. A sample key generation section follows.
If the KeyStore password is specified, then the password mustbe provided for the adapter.
Press RETURN when prompted for the key password (thisaction makes the key password the same as the KeyStore password).
This operation creates a KeyStore file clientkeystore in the current working directory. You must specify a fullyqualified domain for the “first and last name” question.The reason for this use is that some CAs such as VeriSign expect thisproperties to be a fully qualified domain name.
Thereare CAs that do not require the fully qualified domain, but it isrecommended to use the fully qualified domain name for the sake ofportability. All the other information given must be valid. If theinformation cannot be validated, a CA such as VeriSign does not signa generated CSR for this entry.
This KeyStore containsan entry with an alias of client.This entry consists of the generated private key and information neededfor generating a CSR as follows:
This command generates a certificate signing request which canbe provided to a CA for a certificate request. The file client.csr contains the CSR in PEM format.
Some CA (one trusted by the web server to which the adapteris connecting) must sign the CSR. The CA generates a certificate forthe corresponding CSR and signs the certificate with its private key.For more information, visit the following web sites:
or
If the certificate is chained with the CA’scertificate, perform step 4; otherwise, perform step 5 in the followinglist:
Perform the following command.
The command imports the certificate and assumes the client certificateis in the file client.cer and theCA’s certificate is in the file CARoot.cer.
Perform the following command to import the CA’scertificate into the KeyStore for chaining with the client’scertificate.
Perform the following command to import the client’scertificate signed by the CA whose certificate was imported in thepreceding step.
The generated file clientkeystore containsthe client’s private key and the associated certificate chainused for client authentication and signing. The KeyStore and/or clientkeystore, can then be used as the adapter’sKeyStore.
Creating a KeyStore in PKCS12 Format
This section explains how to create a PKCS12 KeyStoreto work with JSSE. In a real working environment, a customer couldalready have an existing private key and certificate (signed by aknown CA). In this case, JKS format cannot be used, because it doesnot allow the user to import/export the private key through keytool. It is necessary to generate a PKCS12database consisting of the private key and its certificate.
The generated PKCS12 database can then be used as the Adapter’sKeyStore. The keytool utility iscurrently lacking the ability to write to a PKCS12 database. However,it can read from a PKCS12 database.
Store Ssh Keys Github
Note –There are additional third-party tools available for generatingPKCS12 certificates, if you want to use a different tool.
For the following example, openssl isused to generate the PKCS12 KeyStore:
The existing key is in the file mykey.pem.txt in PEM format. The certificate is in mycertificate.pem.txt, which is also in PEM format. A textfile must be created which contains the key followed by the certificateas follows:

This command prompts the user for a password. The password isrequired. The KeyStore fails to work with JSSE without a password.This password must also be supplied as the password for the Adapter’sKeyStore password.
This command also uses the openssl pkcs12 commandto generate a PKCS12 KeyStore with the private key and certificate.The generated KeyStore is mykeystore.pkcs12 withan entry specified by the myAlias alias.This entry contains the private key and the certificate provided bythe -in argument. The noiter and nomaciter optionsmust be specified to allow the generated KeyStore to be recognizedproperly by JSSE.
Creating a TrustStore
For demonstration purposes, suppose you have the followingCAs that you trust: firstCA.cert, secondCA.cert,thirdCA.cert, located in the directory C:cascerts. You can create a new TrustStore consistingof these three trusted certificates.
To Create a New TrustStore
Perform the following command.
Enter this command two more times, but for the secondand third entries, substitute secondCA and thirdCA for firstCA.Each of these command entries has the following purposes:
The first entry creates a KeyStore file named myTrustStore in the current working directoryand imports the firstCA certificateinto the TrustStore with an alias of firstCA.The format of myTrustStore is JKS.
For the second entry, substitute secondCA to import the secondCA certificateinto the TrustStore, myTrustStore.
For the third entry, substitute thirdCA to import the thirdCA certificateinto the TrustStore.
Once completed, myTrustStore is available to be used as theTrustStore for the adapter.
